Security Operations Center (SOC)
Cyber Security is not an option!
Protect your organisation against security threats with our state-of-the-art SOC.
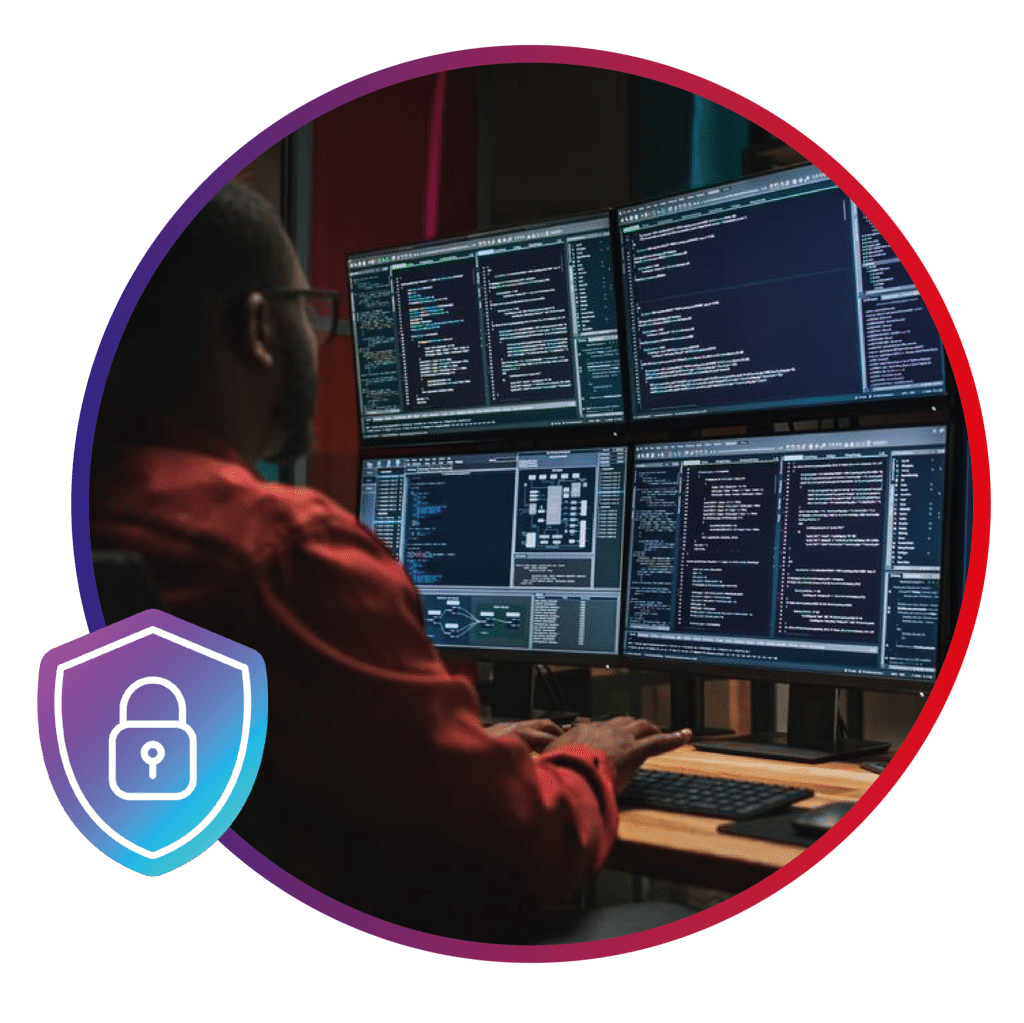
Our mission is to provide you with high-quality IT security.
End-to-end protection for organisations of all sizes.
Presentation
A Security Operations Center (SOC) manages the security and compliance of an organisation's IT systems. At TICANALYSE, we offer a SOC as a service that monitors security threats in real time, detects incidents, analyses security events and provides a rapid and effective response to security incidents.
EXPERTISE
Our SOC as a service offers a number of features, including :
-
Real-time monitoring
Our security team constantly monitors security activities for potential threats.
-
Threat detection
We use advanced threat detection tools to identify security threats as soon as they occur.
-

Response to security incidents
Our security team is ready to respond quickly to manage security incidents and minimise disruption to your business.
-
Analysis of security events
We analyse security events to identify trends and patterns of suspicious behaviour.
-

Safety reports
We provide regular security reports to help you understand the security threats facing your business and the measures we have taken to address them.

services
Intrusion test
Our penetration testing service allows you to test the robustness of your IT infrastructure by simulating targeted attacks. Our IT security experts use advanced methods to identify vulnerabilities in your network, applications and systems, to help you strengthen your cyber security posture.
Penetration tests are designed to help you assess the effectiveness of your security teams. We try to identify possible security problems that could lead to the leakage of sensitive information or to a situation where a malicious user, without the appropriate authorisations, could gain access to sensitive information. Our penetration testing activities fall into one of the following categories:
This is a classic case of verifying a company's security posture by emulating an external attacker attempting to gain unauthorised access to the system. Other activities include attempts to interfere with web application users or impact the system in some other negative way.
The objective of a white-box test is to increase the detection rate of the number of hidden vulnerabilities. Performing a white-box security assessment allows a tester to go further and find vulnerabilities in the target environment and the application's source code.
Combining black-box and white-box technics, the grey-box penetration test is used to check a company's vulnerability to insider attacks. This test simulates an attacker who already has some knowledge of the workings of the company. It takes less time and is more cost-effective than the black box test.

Vulnerability assessment
Vulnerability assessment is an essential process for identifying potential vulnerabilities in your IT environment. Our team of experts carries out an in-depth analysis of your systems, networks and applications, using the latest technics. We then provide you with clear, concrete recommendations for strengthening your security and protecting your sensitive data.
The process:

This involves identifying the critical assets that need to be protected, such as sensitive data, key infrastructure, financial resources, etc.
The various potential threats to which assets are exposed, such as computer attacks, natural disasters, human error, etc., need to be examined.
Once the threats have been identified, it is necessary to determine the vulnerabilities that could be exploited by these threats. This may involve examining existing security measures, weaknesses in systems, processes or policies.
This involves assessing the potential impact on assets if vulnerabilities are exploited. This can include an estimate of financial losses, service interruptions, damage to reputation, etc.
Once the vulnerabilities and potential impacts have been identified, it is important to prioritise the risks according to their severity. This allows resources to be concentrated on the most critical vulnerabilities.
Based on the results of the assessment, appropriate mitigation measures can be developed. This may include actions such as implementing additional security controls, improving policies and procedures, staff training, etc.
Cyber security policy
A sound cyber security policy is the cornerstone of any organisation that is resilient in the face of cyber threats. We can help you design and implement a cyber security policy tailored to your specific needs. Taking into account your infrastructure, processes and business objectives, we develop clear and practical guidelines to protect your digital assets and reduce risk.
The process:
We start by clearly defining the objective of the cyber security policy. Then we specify the systems, data and users affected by the policy. We also specify the laws, regulations or security standards with which your organisation must comply.
We determine the cybersecurity responsibilities of the various players in the organisation. This may include the roles and responsibilities of security staff, managers, employees and end users.
We describe the specific security practices that all employees must follow. This may include using strong passwords, regularly updating software, identifying and managing vulnerabilities, classifying data, etc. We include clear and understandable guidelines.
Specify how access to systems and data is to be managed. Define policies for creating, modifying and deleting user accounts. Specify the rules for using administrative privileges and managing access rights.
Describe the procedures to be followed in the event of a security incident, such as a cyber attack, data breach or security vulnerability. Specify how incidents are to be reported, assessed, managed and resolved. Also include information on data backups and disaster recovery plans.
Based on the results of the assessment, appropriate mitigation measures can be developed. This may include actions such as implementing additional security controls, improving policies and procedures, staff training, etc.
Mention the compliance and audit procedures that will be followed to ensure compliance with cybersecurity policies. This may include regular audits, compliance assessments, security reviews and penetration tests.
Specify that the cyber security policy will be regularly reviewed and updated to reflect new threats, technological changes and regulatory requirements. Also indicate the procedure to be followed for requests to amend the policy.

Disaster recovery plan

A disaster recovery plan is essential to minimize potential disruption in the event of a major incident. Our experienced team will work with you to develop a customized plan to ensure that your business can recover quickly and effectively from an adverse event. We identify critical points of failure, implement preventive measures and recovery procedures, and regularly test the validity of your plan.
DIGITAL FORENSIC SCIENCE
Digital forensic plays a key role in resolving IT security incidents and malicious activity. Our digital forensics experts use advanced technics to collect and analyze digital evidence to identify the perpetrators of attacks, fraud and other criminal activity. We also provide detailed reports and recommendations to strengthen your defence against such threats in the future.
Digital forensic enables the collection and analysis of digital evidence from electronic devices such as computers, mobile phones, tablets, hard drives, servers, etc. We use specialized technics to extract relevant data, such as emails, files, browsing histories, metadata, activity logs, online communications and so. This digital evidence can play a vital role in identifying suspected perpetrators, reconstructing events and solving cybercrime.
Digital forensic is essential for investigating cyber attacks, such as computer intrusions, data theft, online fraud, phishing attacks and so. We can analyse the traces left by attackers in computer systems, such as connection records, log files, IP addresses, malicious signatures and so. These investigations enable us to identify the methods used by attackers, their motivations and the security measures to be taken to prevent future attacks.
Digital forensic ensures that the integrity of digital evidence is preserved throughout the investigation process. We use specialised methods and tools to ensure that digital evidence is collected in a legal, admissible and unaltered manner. This includes rigorous documentation of procedures, chain of custody of evidence, protection against contamination, creation of back-up copies and preservation of data confidentiality. Preserving the integrity of digital evidence is crucial to its valid and reliable use in court.

Incident response
A disaster recovery plan is essential to minimize potential disruption in the event of a major incident. Our experienced team will work with you to develop a customized plan to ensure that your business can recover quickly and effectively from an adverse event. We identify critical points of failure, implement preventive measures and recovery procedures, and regularly test the validity of your plan.
Real-time IT threat map
security team
Our security team is made up of qualified and experienced IT security professionals. All our team members have specific security training and certifications and have hands-on experience in managing security incidents. We pride ourselves on our ability to provide customised security solutions to our customers.
Cybersecurity news





Frequently asked questions
A Security Operations Center (SOC) is a security center that monitors and protects an organization's IT systems, networks and data. It is a command and control center for IT security.
A SOC offers a number of benefits, including real-time monitoring and detection of security threats, rapid response to security incidents, improved regulatory compliance and reduced security risks.
A SOC works by continuously monitoring an organisation's IT systems, networks and data to detect security threats. Security analysts use monitoring and detection tools to identify security incidents and then take action to respond.
A SOC can detect a wide variety of security threats, including phishing attacks, malware, denial of service (DDoS) attacks, brute force attacks and network intrusions.
If you are a customer of our SOC, you can contact our 24/7 support center to report a security incident. If you are not a customer, you can contact us via our website for assistance.
The cost of SOC services can vary depending on the size of the organisation, the level of protection required and the specific services requested. We offer bespoke security solutions to meet each customer's needs, and can provide detailed quotations on request.
Pricing
We offer a range of pricing options for our SOC as a service to meet the needs of organisations of all sizes.
Contact us to find out more about our offers.
contact
If you have any questions or would like to find out more about our SOC as a service, please do not hesitate to contact us at the following addresses:
- [email protected]
-
Somgandé, Sector 19, 1st floor of the building opposite the Clinique Notre Dame de la Paix (Clinique de Jean-Baptiste)
01 BP 726 Ouagadougou 01
We'd be delighted to talk to you and answer any questions you may have.
